On July 5, 2015, an unidentified group of hackers published 400 gigabytes worth of internal data from Italian company Hacking Team (HT), which for a long time has been accused of selling spyware and surveillance software to oppressive governments around the world. Hacking Team’s work in “lawful interception” allowed powerful regimes to actively silence and suppress dissent. Though Hacking Team is now part of the mainstream narrative around privacy and government surveillance, it has long been on the radar for privacy advocates worldwide.
Toronto-based Citizen Lab published extensive research on Hacking Team, including a report in 2012 on the use of their backdoor Remote Control System (RCS)—known as DaVinci—by the Moroccan government to target a citizen journalist group called Mamafakinch, and the arrest of UAE blogger Ahmed Mansoor. Hacking Team’s RCS software allows the user to break encryption, remotely access a computer’s webcam and microphone, and monitor encrypted communications.
The 400GB data dump included details such as exploits for Adobe Flash and Windows operating system. HT knowingly sold software to regimes and governments which were notorious for human rights violations. These include countries such as Sudan, Uzbekistan, and Ethiopia.
On July 8, 2015, Wikileaks published a searchable email directory of all Hacking Team internal communications.
Bolo Bhi has been going through these emails to find out the involvement of Hacking Team in Pakistan. Though we are still filtering through over a thousand emails, we have put together an initial picture of Hacking Team’s interest in Pakistan, and attempts by Pakistani companies to obtain Hacking Team software, possibly for the government.
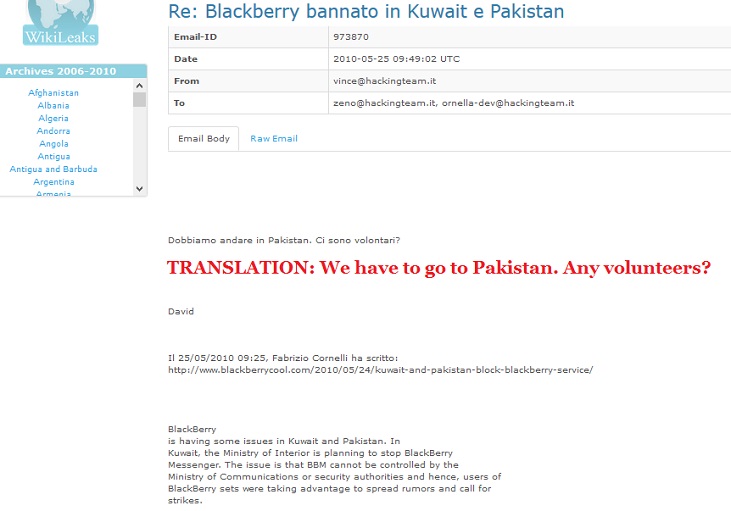
On May 25, 2010, Hacking Team expressed interest in visiting Pakistan after the Pakistan Telecommunication Authority banned Blackberry services:
However, following media coverage of the Raymond Davis case in 2011, Hacking Team had changed its mind. David Vincenzetti, CEO of HT, discussed how Pakistan’s refusal to free Raymond Davis demonstrated the country’s hostility towards Westerners and Americans. He suggested it would be better to meet Pakistani companies in neutral places such as Dubai.
Nonetheless, by January 2011, HT had already been approached by two companies from Pakistan – Zeeshan Zakaria and a company called Miran—pitching similar clients who desire to use HT software; various branches of the Pakistani government or establishment. As two companies cannot pitch the same client, HT discussed the situation internally. This reveals some politics on the part of the Pakistani companies. The email dated January 20, 2011, originally in Italian, roughly translates to this:
“We are already in contact with another partner (Zakaria) who has already brought a security agency and has already requested a new meeting in Dubai.”
The day before yesterday, before the mail Miran sent, Zakaria warned us we would receive requests from other companies asking us to remain silent […] it is therefore likely that Miran is on the same client.
Today we respond and ask who the end user is, and then decide how to proceed.”
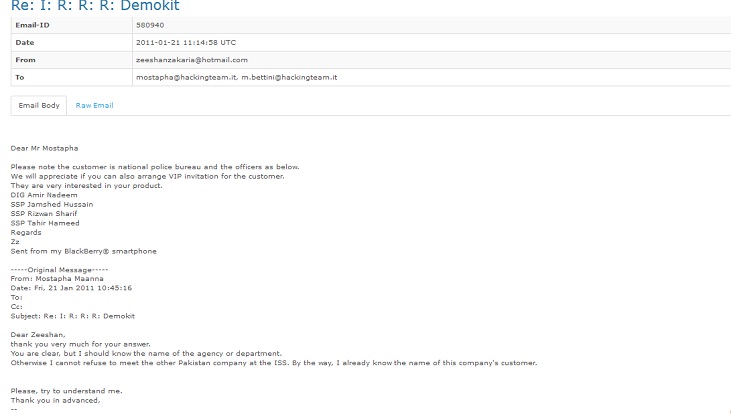
On January 21, 2011, Zakaria shared a list of people who would be meeting with HT and shared details of who his customer was as well.
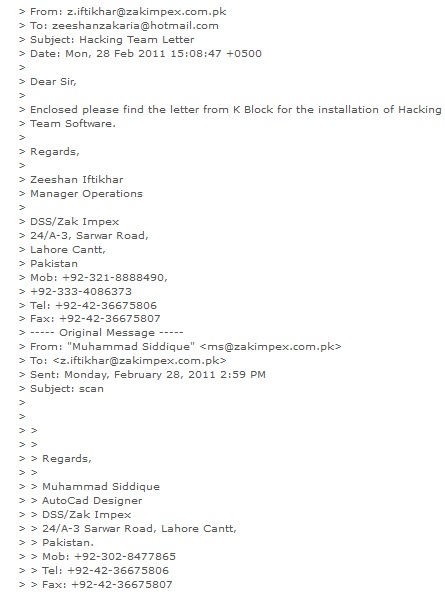
By February 28, 2011, Zakaria received an email from Intelligence Bureau (IB) authorising the installation of RCS software from HT. In January 21, 2011 email, Zakaria had defined the clients as the national police bureau, however, the February 28 communiqué references permission from “K-Block”, the headquarters of the IB at the Secretariat in Islamabad.
Shortly after this exchange, on March 15, 2011 Zakaria emailed HT, telling them his clients included FIA, the Punjab Police, and Customer B; the latter were not interested in procuring HT software via Miran, the company. He also asked HT to arrange a demo of their software.
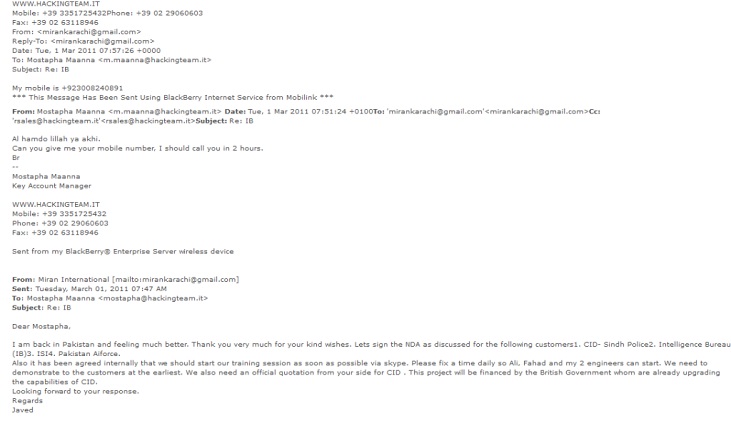
Nonetheless, by March 2011, Miran was also in discussions with HT about procuring services for their clients: the IB, Pakistan Airforce and the Criminal Investigation Department Sindh. Two individuals from Miran were in contact with HT, Ali and Javed. They dealt primarily with Mostapha. Mostapha and Javed seem to be on familiar terms and refer to each other as brother. This did not seem to be out of politeness – in one internal email, Mostapha or “Mus” as his colleagues call him, forwarded an email from Javed to his colleagues and referred to Javed as “fratello,” Italian for brother.
Through their email exchanges, we learnt HT was going to conduct training for Miran’s clients via Skype. Moreover, the project for the CID was, according to Miran, funded by a foreign government as part of ongoing efforts to build CID’s capabilities.
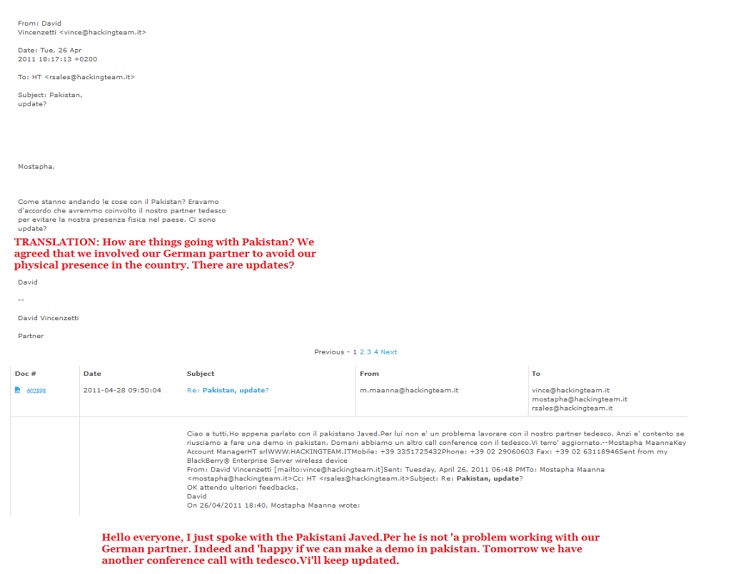
In May 2011, Mostapha updated his seniors regarding the situation in Pakistan who in previous emails indicated their keen interest in gaining the country as a client. He responded (roughly translated below) to an email from the HT CEO:
“Hello David, We talked to our German partner, he’ll go to Pakistan to demos and meetings with clients. Even by Miran (Javed, Pakistani) all seemed ok.
It is all about understanding how to make the agreement with all and the two. Anyway, tomorrow I hear from Javed.”
This seems to be possibly the same Javed who had communicated with Hacking Team on behalf of Miran.
In April, David Vincenzetti had emailed Mostapha asking for updates on Pakistan. Through this exchange, we learn that HT had decided to deal with Pakistani customers through a German partner in order to avoid visiting Pakistan. A man named Javed is happy to work with these German partners.
By June 2011, Ali and Javed from Miran provided Mostapha with more details regarding their customers, and explained that their project was being funded by a foreign government, which had generously donated equipment to one of their customers as well.
The same customer, CID Sindh, had trouble with the technology behind HT’s software, as detailed in an email to Mostapha. Their problem was regarding HT’s Remote Control System (RCS) which only works on smartphones with Wi-Fi and GPRS, whereas Miran’s customers also wanted software that could target old, cheap, basic mobile phones without Wi-Fi, Edge, or GPRS. An internal email dated June 6, 2011 intended to be sent in English to Miran states:
We are sorry, but RCS does not support “cheaper” or “chinese” phones. We support smart phones running Android, BlackBerry, iPhoneOS, WindowsMobile, Symbian only.
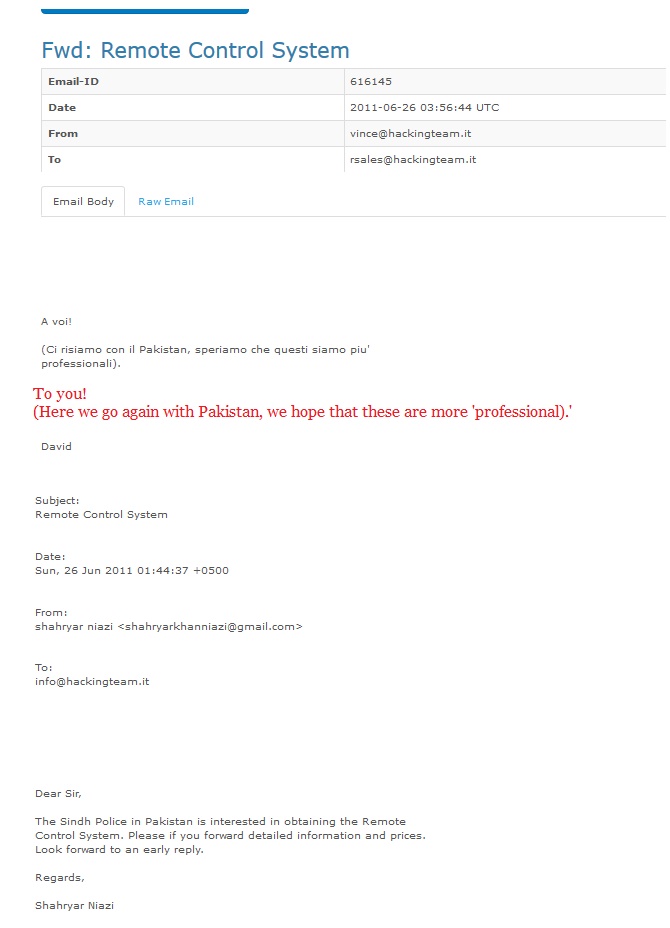
A few days later in June 2011, HT was approached by an individual from Pakistan, who on behalf of Sindh police, was requesting HT’s Remote Control System. David Vincenzetti shared this email with his sales team, expressing hopes that these people would be “more professional” which leads one to speculate that previous discussions with companies like Miran might not have achieved feasible results.
In 2013, HT did not seem to be actively pursued by agents or companies. However, they were in contact with people from RCS Labs for opportunities to work in Pakistan, and planned to have a reseller agreement with RCS.
According to their website, RCS Labs is headquartered in Italy and has affiliates in Spain and France. They describe their work thusly:
RCS has been providing Law Enforcement Agencies worldwide with cutting-edge technological solutions and technical support in the field of lawful interceptionfor more than twenty years.
By September 2013, an agreement had been established between RCS Labs and HT, and they had set up a contact to deal with Pakistan. This communiqué provides a look into the interaction between RCS, HT and a tech consultancy company called A6-Consultancy (with an innocuous looking site) regarding the “right time” to move forward with activities in Pakistan. The emails specially reference changes of director generals at the ISI.
Later in 2013, HT was invited by Pegasus Consultancy to Pakistan for a conference, as well as the IDEAS Expo 2014. It is currently unknown if Hacking Team ever accepted these invitations, but based on their reluctance in previous years, as well as the establishment of agreements with companies like RCS to handle Pakistani requests, we can speculate they might have ignored the invitations.
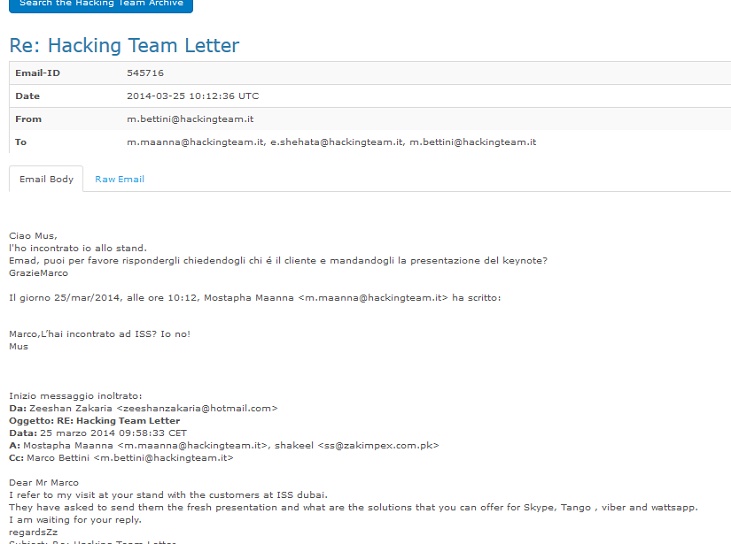
In March 2014, Zeeshan Zakaria was once more in contact with Hacking Team. Based on his email, it becomes clear he had met HT in person, and is following up on previous conversations.
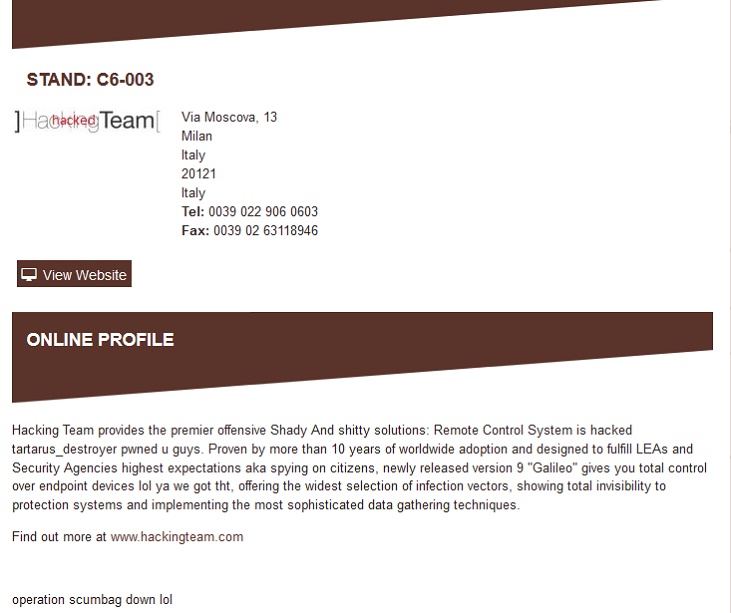
In 2015, Hacking Team clearly made a big impression on Pakistani companies at an event called IDEX. This was clearly the International Defence Exhibition and Conference, held from February 22 to 26 . HT was also on the list of exhibitors at the conference. Their profile page on IDEX seems to have been hacked. This is what it looks like currently:
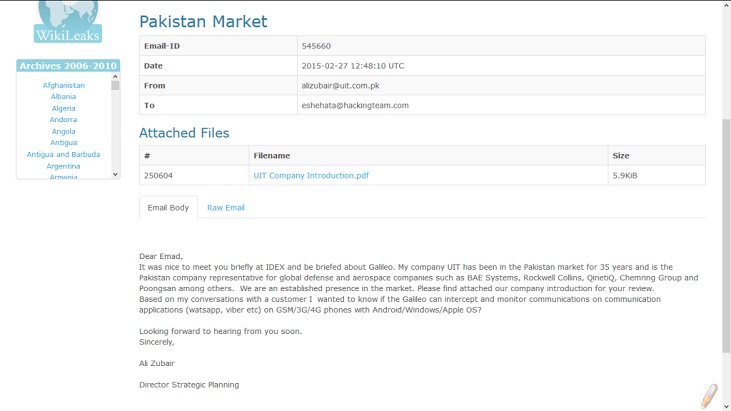
One company which contacted HT from Pakistan was United International Technologies (UIT). Their representative was Ali Zubair,and he spoke primarily with a man identified as Emad Shehata, who is the Key Account manager of of HT in charge of Pakistan. (This detail was gleaned from an email exchange where Shehata introduced himself to a new customer.) Zubair had questions regarding HT’s RCS software, Galileo.
Ali Zubair was still in touch with HT in March 2015, and received a detailed response to his initial inquiry as evidenced by a lengthy email exchange.
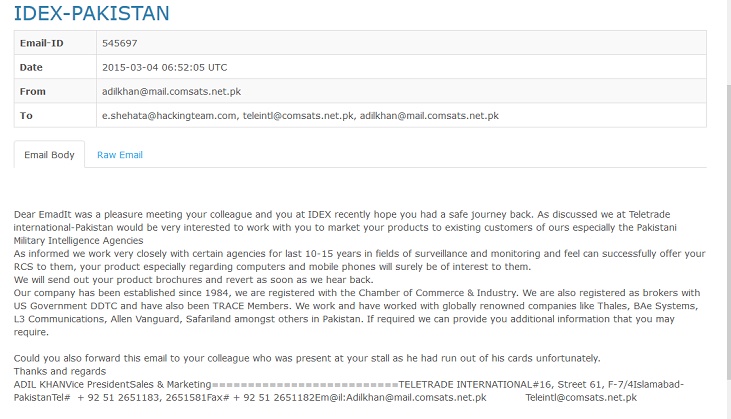
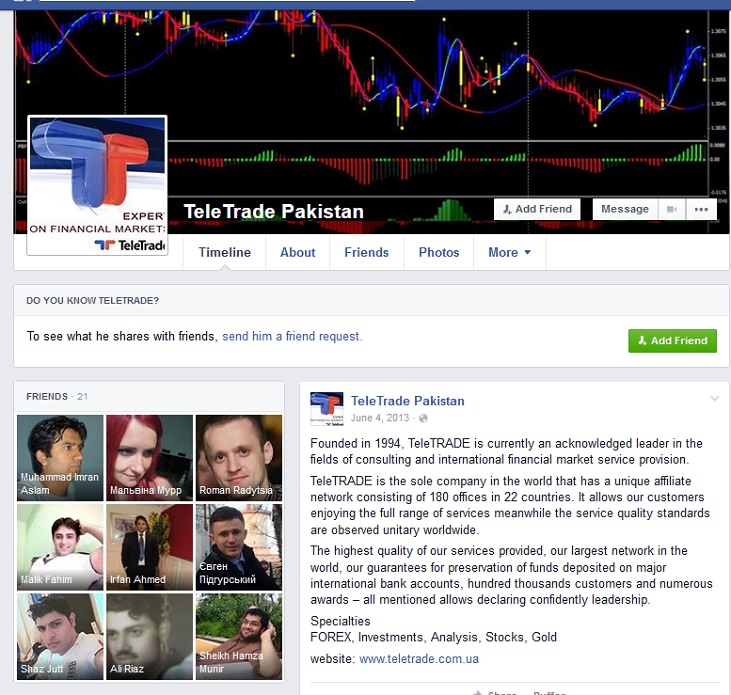
By March 2015, another company from Pakistan had approached Hacking Team. This was Teletrade International, inquiring about HT’s security solutions for their existing list of clients.
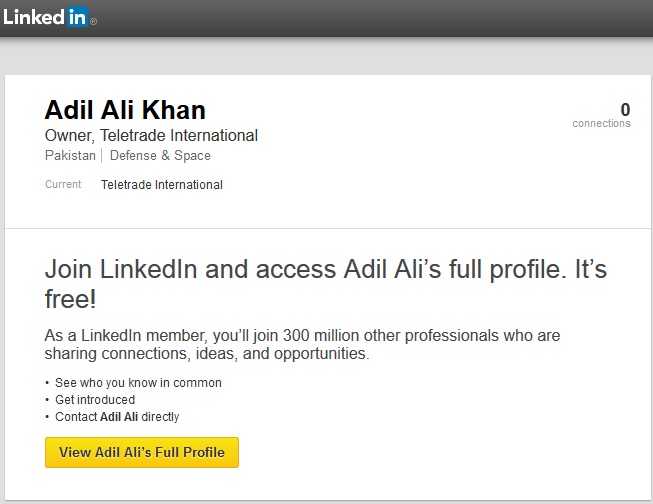
Teletrade also has a Facebook profile, and Adil Khan, the person who contacted HT on behalf of Teletrade, is also on LinkedIn.
According to his LinkedIn profile, Adil Khan is the owner of Teletrade.
HT then invited Teletrade to visit their booth at a conference in Dubai, called ISS Dubai 2015 held on March16 to 18. According to the email thread, Teletrade had declined the offer, and it is uncertain whether Teletrade responded to HT’s request to sign a non-discloser agreement (NDA). The NDA was standard protocol within HT and all companies were asked to sign it when they made initial contact with HT, before proceeding into further discussion or negotiations.
The ISS Dubai conference was actually ISS WORLD Middle-East Conference. According to their website,
ISS World Middle East is the world’s largest gathering of Middle East Law Enforcement, Intelligence and Homeland Security Analysts as well as Telecom Operators responsible for Lawful Interception, Hi-Tech Electronic Investigations and Network Intelligence Gathering.
According to the agenda of the conference, HT conducted a number of sessions in the training track Lawful Interception and Criminal Investigation Training. These includedToday’s Interception in an encrypted, social and clouded world and Demystifying SSL/TOR Interception: Attack case history and state-of-art countermeasures. In the training track Encrypted Traffic Monitoring and IT Intrusion Product Training, they conducted sessions on HackingTeam and Its Competitors: IT Offensive Surveillance in Today’s Changing, Challenging and Dangerous World and Intruding Personal Devices with Remote Control System: Live Demo of Latest Attack and Data Gathering Techniques.Companies like Finfisher and The Gamma Group also conducted several sessions at the conference, based on the agenda. RCS s.p.a, which as mentioned earlier was partnering with HT to handle accounts in Pakistan, was also a sponsor at ISS.
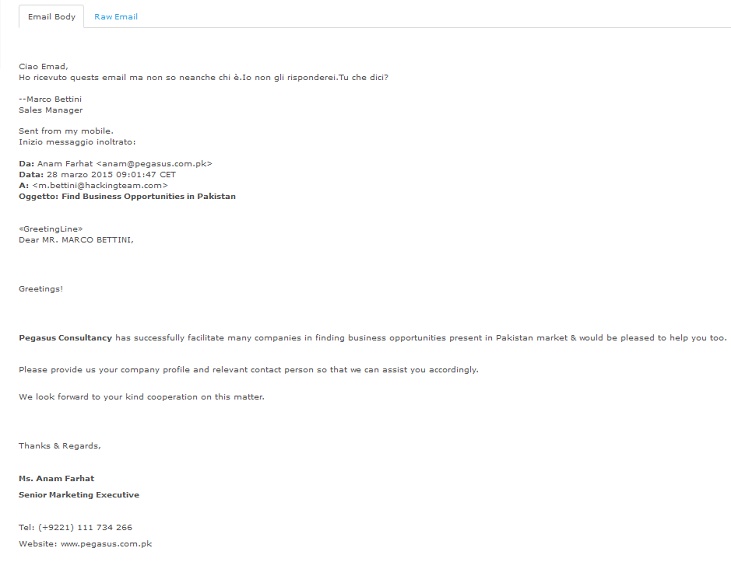
On March 28, Pegasus Consultancy contacted HT once more, this time as a follow-up to meeting HT at IDEX as well.
According to their website, Pegasus Consultancy aims to facilitate the transaction process between buyers and sellers. There does not seem to be any further correspondence between Pegasus Consultancy and HT.
Based on the emails Bolo Bhi has gone through, it seems Hacking Team has been in contact with Pakistani companies for years. There have been several meetings as well as demonstrations of software, but there was never any concrete deal reached.
However, this is not a confirmation that HT software has not been used in Pakistan, either in the past or present. It is however, quite clear there has been interest from various quarters (official and otherwise) in acquiring HT software. Whether it is acquired and used in the future remains to be seen. What we do know, beyond the Hacking Team revelations, is that state-level surveillance does not end here. According to a report published by Privacy International, Pakistan has received foreign funding to create a surveillance system, which is used to surveil ordinary citizens. Furthermore, it is also a third-party partner to NSA, and the relationship is described as long-term, based on mutual trust and cooperation. In wake of this report, as well as the HT email dump, we believe it is necessary to challenge the legality of such surveillance, as well as pushing for legislation that protects human rights from a surveillance perspective.
This article was originally published here and the featured image was taken from pixabay.