The National Computer Emergency Response Team (CERT) has released an alert on a new and complex cyber threat that is affecting users in the region. New threat intelligence shows that cybercriminals are using fake CAPTCHA verification pages to download malware to the targeted users’ computers using social engineering.
Mechanism of the attack
When users search for free content, they are taken to other sites that display fake CAPTCHA scams. When the users engage with these fake verifications, they run scripts that are destructive to their systems. This advisory outlines the technical steps of the attack, key indicators of compromise (IOCs), and preventive measures that organizations should take to protect their networks.
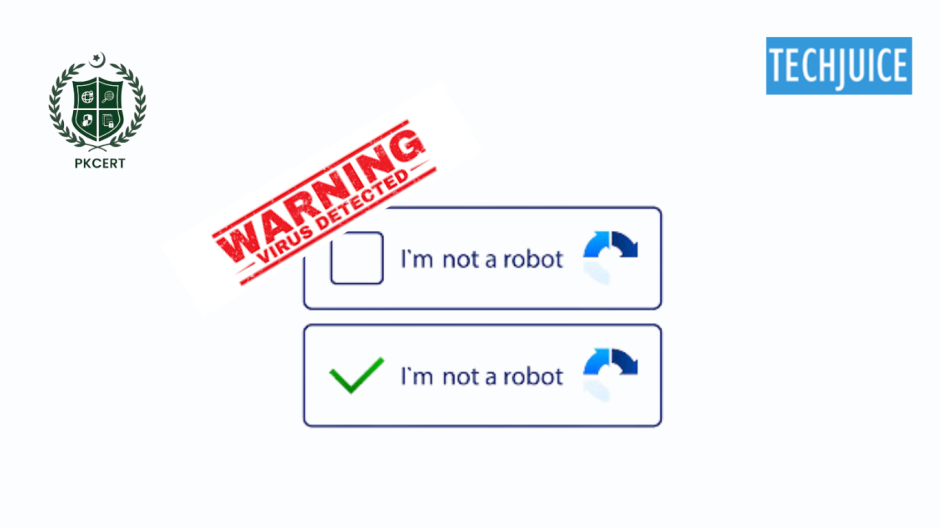
The cyber campaign includes fake CAPTCHA pages that look like real processes. When the user clicks the “I’m not a robot” button, a script is pasted into the victim’s clipboard, followed by further instructions that lead the user into executing code through the Run dialog. The attack mainly focuses on PowerShell to download other malware such as infostealers and network scanners that can penetrate the victim’s network.
Indicators of compromise
Several malicious behaviors are identified in the study, including redirecting to other sites that offer free content such as movies, which are behind CAPTCHA verification. The users are presented with a fake CAPTCHA and when they interact with it, a script drops a malicious PowerShell command into the clipboard. When executed it opens a new window and enables the attackers to download more malicious files from their server. Indicators of compromise include several malicious URLs and specific SHA256 hashes of the known malware payloads.
The NCERT has implemented numerous preventive measures to mitigate this hazard. One of the most critical components of user education is to educate employees on the hazards of copying and pasting unfamiliar commands. It is recommended that organizations implement a robust endpoint protection solution that can detect and prevent PowerShell-based attacks, as well as monitor the network traffic connection.
In addition to the implementation of EDR to monitor suspicious activity, particularly that involving PowerShell, certain response actions include the blocking of the identified malicious domain in organization firewalls. Additionally, to prevent business interruptions, the author recommends conducting daily data backups and comprehensive upgrading.
NCERT has emphasized the necessity of being vigilant against social engineering strategies that exploit individuals’ confidence in traditional web interactions in light of these developments. The highlighted security measure should be implemented by numerous organizations, particularly those in the government and public sectors, in order to mitigate this emerging cyber threat. In order to mitigate these forms of malice, it is essential to control and continuously supervise such activities, implement secure endpoint security, and conduct training and awareness sessions for users.