Since the Microsoft Exchange vulnerabilities have still not been fixed, the Chinese hackers are taking advantage of the slowness of patching being done to end the vulnerabilities. According to Check Point Research (CPR) findings, a cybersecurity division, the hacking groups continue to exploit four zero-day vulnerabilities actively. The post says, “In the past 24 hours, the team has observed exploitation attempts on organizations doubling every two to three hours.”
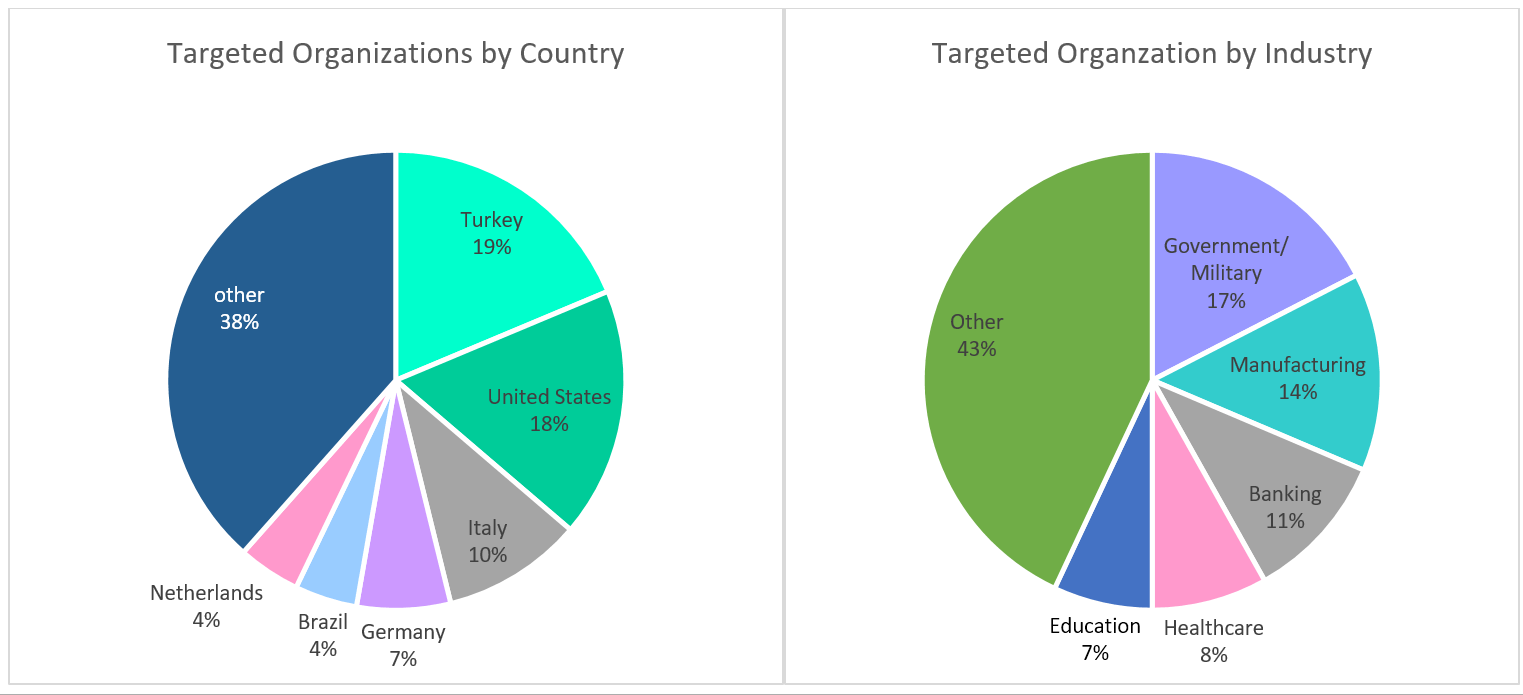
“Global experts are using massive preventative efforts to combat hackers who are working day-in and day-out to produce an exploit that can successfully leverage the remote code execution vulnerabilities in Microsoft Exchange.”, the blog by Check point added.
Microsoft has accused Chinese advanced persistent threat (APT) group Hafnium of being the mastermind behind the ongoing attack, which has since seen the involvement of at least 10 APT groups.
A blog post from Microsoft said, “Hafnium operates from China, and this is the first time we’re discussing its activity. It is a highly skilled and sophisticated actor. Historically, Hafnium primarily targets entities in the United States for exfiltrating information from several industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks, and NGOs.”
Apart from the Microsoft Exchange servers breach, the US is also reeling from the effects of the SolarWinds software cyberattack.
Read More: Chinese-based hackers hack more than 60,000 Microsoft Exchange Servers.