In recent news, a loophole in WhatsApp has been determined where an attacker can completely suspend a user’s WhatsApp account where all is needed is the user’s phone number. Presently, there is no known solution for the issue.
This newly-discovered flaw primarily uses two separate vectors where the attacker installs WhatsApp on a new device and ends up entering your number to activate the respective chat service. Due to the two-factor authentication system, the attacker can not verify as the system sends the logic prompts to your phone. Once the attacker has attempted to login in multiple times and fails, your own login will be locked for the next 12 hours.
With the user’s account locked, the attacker can send a support message to WhatsApp from their email address where they claim your account as their own and inform WhatsApp that your phone had been lost or stolen and the WhatsApp account associated needs to be deactivated. The service then verifies this with an email reply and ends up suspending your own account. The attacker repeats this process to ensure that your account is permanently deactivated.
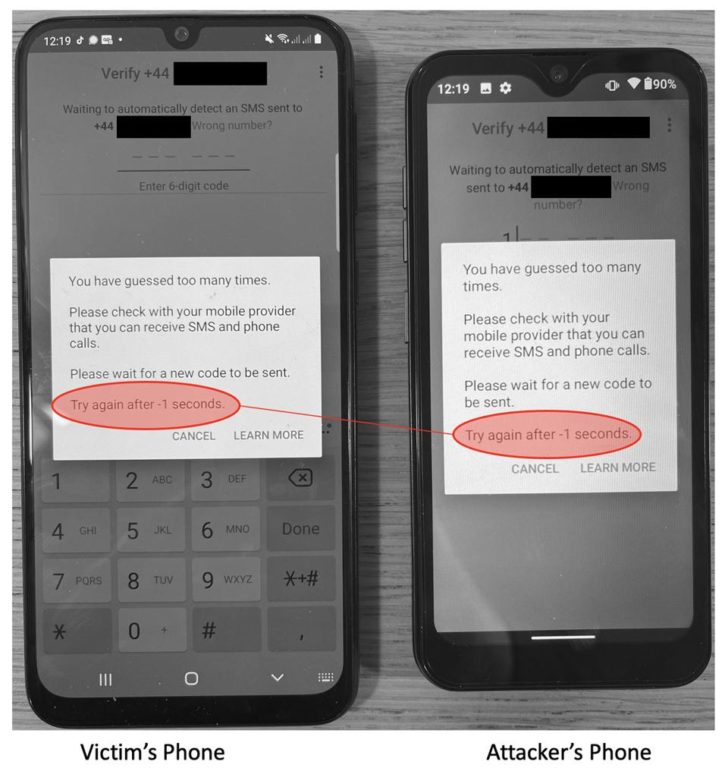
This attack was initially determined by security researchers Luis Márquez Carpintero and Ernesto Canales Pereña who had properly tested the method. At the end of the day, the results were disturbing though it is to be noted that this method can’t be used to actually gain access to an account, merely to block access by its legitimate owner. Confidential text messages and contacts are not exposed.
Currently, WhatsApp is working out a solution to fix this loophole until then one of their representatives suggested that providing an email address with your two-factor authentication credentials can help avoid this hypothetical scenario.












